 The pandemic has kept people stuck at home, and in front of their computers…which has brought out nefarious characters finding new twists on old scams.
The pandemic has kept people stuck at home, and in front of their computers…which has brought out nefarious characters finding new twists on old scams.
Another scam…another newsletter to help you avoid being taken advantage of, or worse, losing your data and money. Hackers are now preying on vulnerable people to commit online fraud, using the old ‘tech support’ scam that has bilked people out of billions of dollars for the last several years.
What’s new is that now scammers are targeting more people over the age of 60 via their computers as they spend more time online. The FTC also reports fraud losses totaled $388 million through the third quarter of 2020, a number that’s up 23% from 2019!
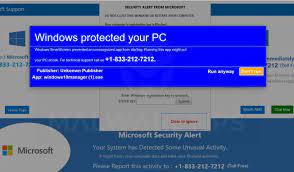
Scammers are using realistic looking pop-ups on Macs and PC’s alerting you to a virus or issue with your system, and providing a phone number to call. This should be your first red flag…Not to make light of the situation, but when was the last time a company gave you an actual customer service phone #?!?
Once they get you on the phone, the real scam begins as they will assure you that they are a certified Microsoft technician (or a tech from Apple, or any other well-known company), and may request access to your system via TeamViewer (or other screen sharing device).
These scams have become so popular that Microsoft and Apple are now warning about various iterations of this scam on their websites. But, unfortunately, the tricks of cyber thieves are constantly evolving and becoming more convincing. Here are some tips on how you can avoid these scams in the future:
• Apple, Microsoft, and other reputable tech companies do not ever contact customers about “tech support,” unless the customer initiates communication. EVER!
• If a pop-up or error message appears with a phone number, don’t call the number. Error and warning messages never include phone numbers!
• If you get a tech support scam pop-up, close your browser immediately. On a Windows PC, press Control-Alt-Delete to bring up the Task Manager. On a Mac, click on the Apple icon in the upper left corner of your screen and use the Force Quit command.
• Never pay for tech support or other services with a money transfer app, gift card, cash reload card, or wire transfer. The only tech support you should be paying for is from ProActivist Computer Support. (wink, wink)
• If you get a call after the pop-up, do NOT answer. If you answer, hang up, and block the call. Once scammers know they have reached a working number, you become a recurring target. One of the most common scams after you engage with cyber-crooks over fraudulent services is the “refund scam.”
• Never trust any company that requests personal or financial information.
• Keep your security software, browser, and operating system up -to-date, and consider using your browser’s pop-up blockers (if you have turned these off previously).
As always, this newsletter is for informational purposes, but I am available to answer any questions or to discuss more about these types of scams. It might also be a good time to for us to review your security settings, and ensure that you are doing everything you can to protect your business (and personal) information.
Andy



 You may not know this yet, but if you use Amazon devices in your home, you should keep reading…
You may not know this yet, but if you use Amazon devices in your home, you should keep reading… The pandemic has kept people stuck at home, and in front of their computers…which has brought out nefarious characters finding new twists on old scams.
The pandemic has kept people stuck at home, and in front of their computers…which has brought out nefarious characters finding new twists on old scams.



